Blog
Beware of Emerging Threats: QR Code Malware Attacks Via Spam Emails

In the ever-evolving landscape of cyber threats, it's crucial to stay vigilant and informed about emerging attack vectors.
Recently, cybersecurity experts have detected a novel threat that exploits a common mobile device feature: QR codes.
These attacks are being delivered through well-designed spam email messages or public QR codes that are pasted over an existing code, and they pose a significant risk to the security of your mobile device.
In this post, we'll explore this new attack vector and provide essential tips to protect yourself.
A New Challenge Arises
As the digital world continues to evolve, cybercriminals are continually innovating to find vulnerabilities to exploit.
One such innovation that has come with the increased use of QR codes since the COVID pandemic, is the use of QR codes to deliver malware onto mobile devices.
This technique is called Qishing (QR Phishing).
A QR code is a code consisting of an array of black and white squares, typically used for storing URLs or other information for reading by the camera on a smartphone.
This approach is particularly insidious because it leverages a feature that many of us use regularly and trust without question.
Email Filters Fall Short Against QR Codes
Most of us rely on email filters to weed out spam and potentially harmful messages.
However, when it comes to QR codes embedded within emails, these filters often prove inadequate.
Because the QR code is an image within the body of the email rather than text, basic email filters often don’t recognize them as a threat.
Cybercriminals are capitalizing on this vulnerability to undermine our trust in email communications.
The Golden Rule: Never Scan Unsolicited QR Codes
The primary rule to thwart these attacks is simple yet paramount: never scan a QR code from an unsolicited email.
This includes email and random QR codes in public.
It is essential to exercise caution, especially when QR codes appear in emails from unverified sources.
These malevolent QR codes are the gateway to malware installation on your mobile devices, posing a significant threat to your organization’s security and data integrity.
Vigilance Against Spoofed Sender Email Addresses
Cyber adversaries are becoming increasingly adept at impersonating legitimate sources.
When your business receives an email containing a QR code, scrutinize the sender's email address meticulously.
In most instances, these addresses will be spoofed to mimic trusted sources.
It is imperative not to be deceived by appearances; always validate the authenticity of the sender before taking any action.
Immediately Delete Unsolicited Emails With QR Codes
To mitigate potential threats effectively, adopt a cautious approach.
If your business receives an unsolicited email housing a QR code, promptly delete it.
Do not entertain the thought of scanning the code, regardless of how enticing the email's content may appear.
The security of your business should always take precedence.
Check That A Physical QR Code Hasn’t Been Tampered With
Sometimes these criminals will paste a QR code containing malware over legitimate QR codes.
If your local restaurant, bank, or parking meter is using QR codes, make sure you’re scanning from their original printed QR code and not something pasted over it.
Verify The URL
When you scan a QR code, oftentimes it will display the URL that it is linking to.
Even if everything seems legitimate about the source of the code, make sure that it is directing you to the website URL that you want to go to.
This will help protect you if someone has taken over the account of a trusted source.
Illustrating The Threat: A Spam Email With A QR Code
To provide a tangible example, here is a spoofed email that is made to look like it came from Microsoft.
It's telling the recipient that they need to scan the QR code to renew their two-factor identification or they may have an interruption in the Microsoft tools they use every day.
In reality, the QR code will either download malware onto their phone or ask them to provide sensitive information such as passwords which may give the cybercriminal access to not only their Microsoft account but possibly other sensitive info as well.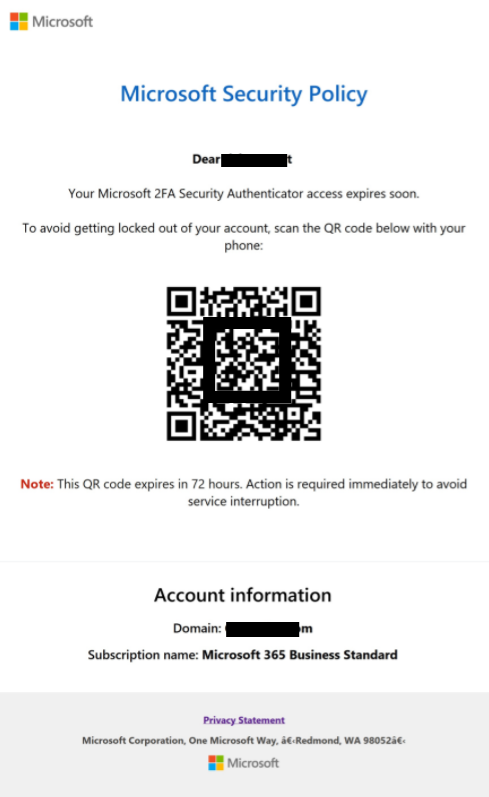
Always remember that such emails are meticulously crafted to deceive and compromise your business's security.
Providing Comprehensive Training for Your Staff
In the face of evolving cyber threats, the importance of cybersecurity education for your staff cannot be overstated.
Equip your employees with the security awareness knowledge and skills they need to identify and mitigate threats like QR code attacks, phishing attempts, ransomware, social engineering, and more.
Conduct regular training sessions to keep them up-to-date with the latest cybersecurity best practices.
Here are some key training topics to consider:
- Phishing Awareness: Teach your staff how to recognize phishing emails and avoid falling victim to fraudulent schemes.
- Ransomware Prevention: Provide guidance on how to prevent ransomware attacks by avoiding suspicious downloads and attachments.
- Social Engineering Defense: Help your employees understand social engineering tactics and how to protect sensitive information from manipulative attackers.
- QR Code Safety: Educate your team on the risks associated with scanning QR codes from unverified sources, emphasizing the importance of caution.
- Incident Response: Train your staff on the appropriate steps to take in case of a security incident, ensuring a swift and effective response.
By investing in cybersecurity training, you empower your staff to become a valuable line of defense against a wide range of cyber threats.
An informed and vigilant workforce is an invaluable asset in maintaining the security and integrity of your business.
Conclusion
The emergence of QR code malware attacks via spam emails underscores the importance of staying informed and proactive in the realm of cybersecurity.
As your dedicated cybersecurity partner, we emphasize the significance of staying vigilant in the face of evolving cyber threats and arming your staff with the knowledge they need to defend your business.
By following the guidelines outlined in this post and providing comprehensive training for your staff, your business can fortify its defenses and effectively mitigate the risks associated with this emerging threat and others in the ever-changing landscape of cybersecurity.
Cybersecurity is an ongoing battle, and your business's proactive stance is your most potent defense against evolving threats.
Furthermore, it's crucial to establish a continuous monitoring and adaptation strategy, as cyber threats are ever-evolving.
By regularly assessing and refining your cybersecurity measures, your organization can maintain a strong defense and adapt to the changing tactics employed by malicious actors, ensuring the long-term security of your valuable assets and data.
Sources:- https://perception-point.io/blog/qr-code-red-quishing-attacks-and-how-to-prevent-them/
- https://www.infosecurity-magazine.com/opinions/qr-codes-vulnerability-cybercrimes/
- https://www.csoonline.com/article/569957/how-attackers-exploit-qr-codes-and-how-to-mitigate-the-risk.html
Read On
Integrity Technology Solutions Recognizes Cybersecurity Awareness Month With Commitment To Online Safety And Education
Bloomington, IL — Oct. 1, 2025 — Integrity Technology Solutions is proud to announce its...
CAT Sunset: What The August 2025 Deadline Really Means For Financial Institutions
If you built your cybersecurity program around the FFIEC Cybersecurity Assessment Tool (CAT), you...
Gone Phishing: How To Avoid The Greatest Cybersecurity Scam
More people fell victim to phishing and spoofing scams in 2024 than any other cybersecurity threat,...


Leave a Reply